Are you wanting to find 'ethical hacking thesis'? Here you can find questions and answers on the topic.
Honorable hacking is i of the tools that are ill-used to judge the security programs of the organizations. Information technology is also referred as penetrating examination, red teaming, encroachment testing, vulnerability and even security judgments. Each one these has different meanings in different countries.
Table of contents
- Ethical hacking thesis in 2021
- Ethical hacking course
- Ethical hacking and cyber security pdf
- Ethical hacking dissertation ideas
- Ethical hacking concepts
- Ethical hacking wikipedia
- Ethical hacking essay pdf
- Is ethical hacking ethical
Ethical hacking thesis in 2021
 This image representes ethical hacking thesis.
This image representes ethical hacking thesis.
Ethical hacking course
 This image illustrates Ethical hacking course.
This image illustrates Ethical hacking course.
Ethical hacking and cyber security pdf
 This image demonstrates Ethical hacking and cyber security pdf.
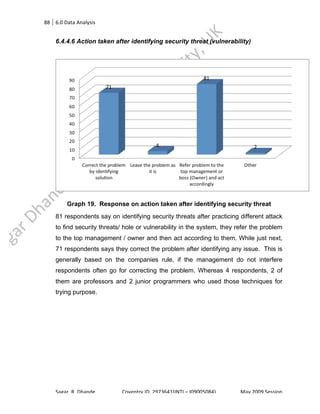
This image demonstrates Ethical hacking and cyber security pdf.
Ethical hacking dissertation ideas
 This picture representes Ethical hacking dissertation ideas.
This picture representes Ethical hacking dissertation ideas.
Ethical hacking concepts
 This picture shows Ethical hacking concepts.
This picture shows Ethical hacking concepts.
Ethical hacking wikipedia
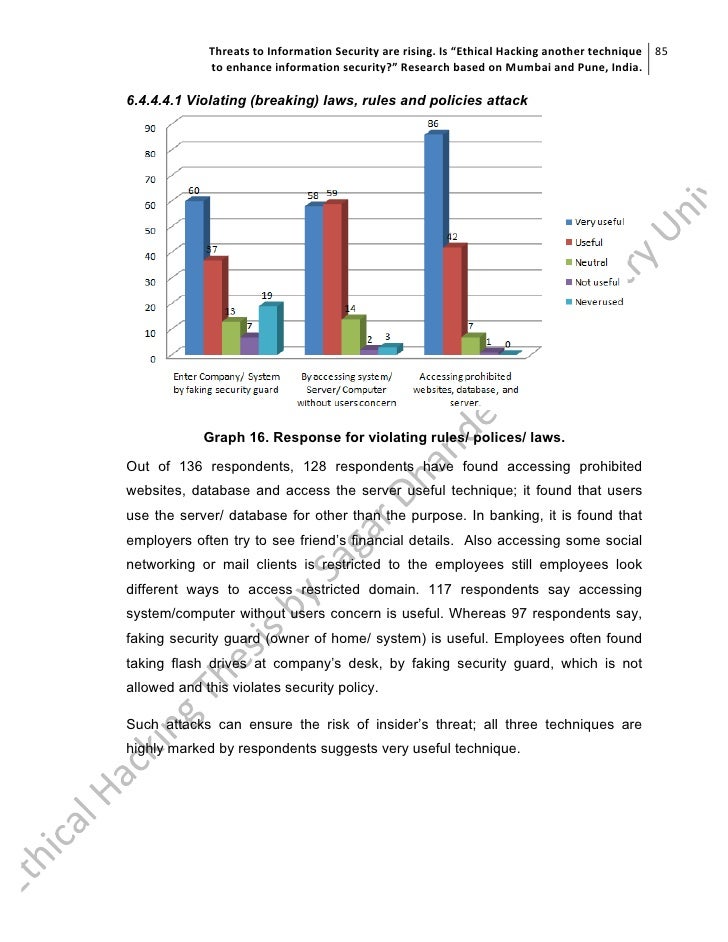 This image demonstrates Ethical hacking wikipedia.
This image demonstrates Ethical hacking wikipedia.
Ethical hacking essay pdf
 This image representes Ethical hacking essay pdf.
This image representes Ethical hacking essay pdf.
Is ethical hacking ethical
 This image representes Is ethical hacking ethical.
This image representes Is ethical hacking ethical.
What are the skills of an ethical hacker?
Successful ethical hackers possess a variety of skills. First and foremost, they must be completely tr ustworthy. While testing secret. In many c ases, this information, if publicized, co uld leading to f inancial losses. During an evaluation, th e ethical
Why is ethical hacking a concern for businesses?
Ethical hacking-also known as penetration testing or intrusion testing or red teaming has become a major concern for businesses and governments. Companies are worried about the possibility of being " hacked " and potential customers are worried about maintaining control of personal information. [1]
How is ethical hacking similar to bookkeeping records?
At the same time, the potential customers social security numbe rs and home addresse s. into th eir computer systems. This scheme is similar to having bookkeeping records. In the case of computer security, th ese damage the t arget systems nor steal information. Instead, they
Who is the author of ethical hacking using penetration testing?
Recommended Citation Koopari Roopkumar, Bharath Kumar, "Ethical Hacking Using Penetration Testing" (2014). LSU Master's Theses. 3238.
Last Update: Oct 2021